Here is some experience around the setup of an OpenVPN site-to-site connection from Ubuntu 20.04.2 LTS to UniFi Security Gateway (USG) written down.
Preparation
UniFi Security Gateway
| Public IP address | 1.1.1.1 |
| Local subnet | 192.168.1.0/24 |
| Local IP address | 192.168.1.1 |
Ubuntu 20.4.2 LTS
| Public IP address | 4.4.4.4 |
| Local subnet | 192.168.4.0/24 |
| Local IP address | 192.168.4.1 |
To setup an OpenVPN site-to-site VPN on the UniFi Security Gateway access is needed to the UniFi Network Controller 6.0.45 console. To generate the needed preshared key you need access to the USG using SSH. These steps are based on the UniFi Network Controller 6.0.45 and the Classic UI.
Preshared Key
- Connect to the USG using SSH, e.g.
$sshuser@192.168.1.1 - Generate the OpenVPN preshared key
$generate vpn openvpn-key /tmp/ovpn
- Copy the key between
—–BEGIN OpenVPN Static key V1—–
and
—–END OpenVPN Static key V1—–
and remove the newlines for the USG configuration. - Save the whole /tmp/ovpn file content for the Ubuntu configuration.
UniFi Security Gateway Configuration
- Login to the UniFi Network Controller and open the Settings in the Classic UI

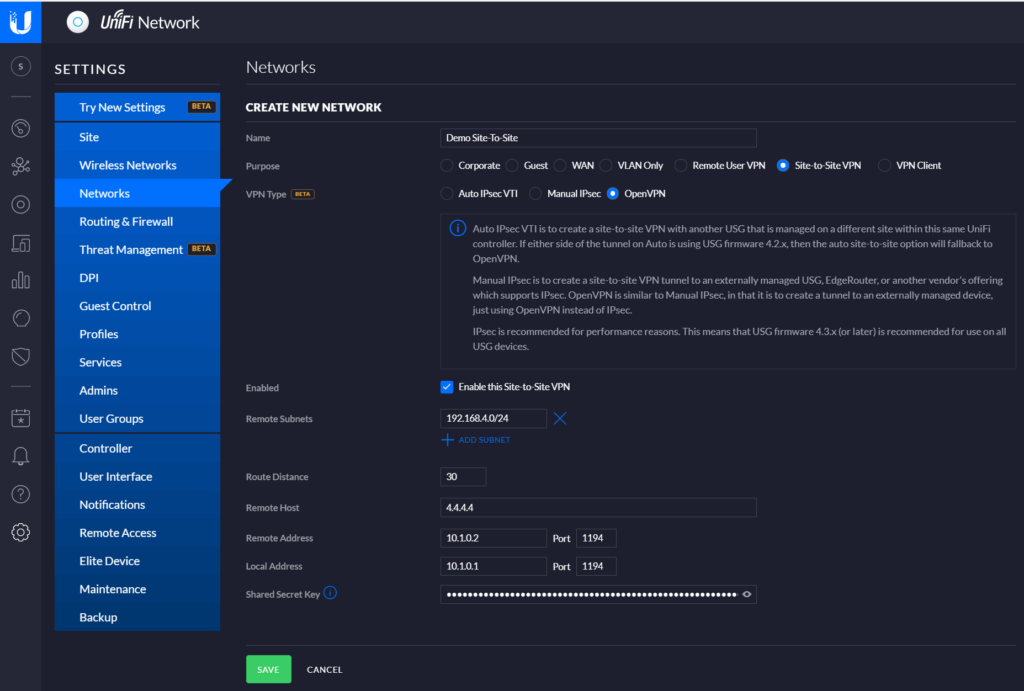
- Open “Networks” and press

- Select “Site to Site VPN” as purpose and choose OpenVPN as type. Fill in the form as showed in the picture below. The preshared key we generated in the last section can now be entered here.
- Save the network
Ubuntu 20.04.2 LTS Configuration
Access the Linux on a shell. You will need sudo permissions.Install OpenVPN
Install OpenVPN
$ sudo apt install openvpnEnable IP Forwarding
$ sudo cat >> /etc/sysctl.conf << EOF
net.ipv4.ip_forward = 1
net.ipv6.conf.all.forwarding = 1
net.ipv4.conf.all.accept_redirects = 0
net.ipv4.conf.all.send_redirects = 0
EOF
$ sudo sysctl -pConfigure Firewall
Add the following text at the beginning of the file /etc/ufw/before.rules before everything else:
*nat
:POSTROUTING ACCEPT [0:0]
-A POSTROUTING -s 192.168.1.0/24 -d 192.168.4.0/24 -j MASQUERADE
COMMIT$ sudo ufw disable
$ sudo ufw enableOpenVPN Configuration File
Create the configuration file /etc/openvpn/server/demo-vpn.conf with the following content:
#
# Sample OpenVPN configuration file for
# office using a pre-shared static key.
#
# '#' or ';' may be used to delimit comments.
# Use a dynamic tun device.
# For Linux 2.2 or non-Linux OSes,
# you may want to use an explicit
# unit number such as "tun1".
# OpenVPN also supports virtual
# ethernet "tap" devices.
dev tun42
remote 1.1.1.1
ifconfig 10.1.0.2 10.1.0.1
script-security 3
# Our up script will establish routes
# once the VPN is alive.
up ./demo-configure-routes.up
# Our pre-shared static key
secret demo-preshared.key
# OpenVPN 2.0 uses UDP port 1194 by default
# (official port assignment by iana.org 11/04).
# OpenVPN 1.x uses UDP port 5000 by default.
# Each OpenVPN tunnel must use
# a different port number.
# lport or rport can be used
# to denote different ports
# for local and remote.
;port 1194
# Downgrade UID and GID to
# "nobody" after initialization
# for extra security.
; user nobody
; group nobody
# If you built OpenVPN with
# LZO compression, uncomment
# out the following line.
; comp-lzo
# Send a UDP ping to remote once
# every 15 seconds to keep
# stateful firewall connection
# alive. Uncomment this
# out if you are using a stateful
# firewall.
; ping 15
# Uncomment this section for a more reliable detection when a system
# loses its connection. For example, dial-ups or laptops that
# travel to other locations.
ping 15
ping-restart 45
ping-timer-rem
persist-tun
persist-key
# Verbosity level.
# 0 -- quiet except for fatal errors.
# 1 -- mostly quiet, but display non-fatal network errors.
# 3 -- medium output, good for normal operation.
# 9 -- verbose, good for troubleshooting
verb 3Save the content of the generated OpenVPN key (/tmp/ovpn on USG) to the file /etc/openvpn/server/demo-preshared.key
Create the file /etc/openvpn/server/demo-configure-routes.up with the following content:
#!/bin/sh
route add -net 192.168.1.0 netmask 255.255.255.0 gw $5and make it executable
$ sudo chmod +x /etc/openvpn/server/demo-configure-routes.upFinishing up
Start the VPN with
$ sudo systemctl start openvpn-server@demo-vpn.serviceTo inspect the status call:
$ sudo systemctl status openvpn-server@demo-vpn.serviceTo start the site-to-site VPN at boot:
$ sudo systemctl enable openvpn-server@demo-vpn.serviceTest the VPN
Try ping the USG through the tunnel:
$ ping 10.1.0.1